
Security
Firewall
Our firewall is setup as a separate machine that acts as a gateway for access to all other servers in our system. This firewall is designed to prevent hackers from entering the system searching files and information. The firewall acts as a barrier so that we only have a single point of entry to our system... through the web browser. All of our internal databases and applications are shielded from any access outside the firewall.
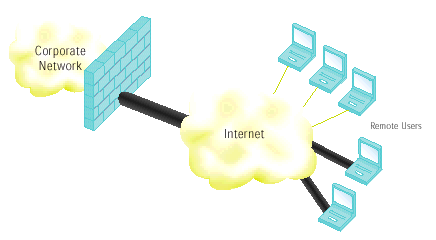
We use the Check Point VPN-1 solution to provide state-of-the-art security for critical client resources. For users of remote access VPNs, Checkpoint leads the industry with advanced client solutions to establish VPN connections efficiently and completely transparently and provides strong encryption to ensure data privacy, and supports a broad range of authentication methods to verify user identity. All VPN-1 client solutions secure communications with network gateways and with individual servers.
Check Point FireWall-1 is based upon Stateful Inspection, the de facto standard for Internet firewalls invented by Check Point Software Technologies (U.S. Patent No. 5,606,668 and 5,835,716). Stateful Inspection provides the highest level of security possible by incorporating communication- and application-derived state and context information, which is stored and updated dynamically.
FireWall-1 transparently authenticates users of HTTP services via an extended log-in procedure. Transparency means that the user can request a connection directly to the final destination, rather than to a firewall gateway. FireWall-1 automatically intercepts each connection and prompts users to authenticate themselves if required by the security policy.
Check Point FireWall-1 protects users from virus attacks, malicious Java and ActiveX applets and undesirable Web content through its integrated content security capabilities: Integrated Security Servers. For each connection established through a FireWall-1 HTTP, SMTP or FTP security server, the network manager controls access to specific resources with a high degree of granularity. Access can be controlled to specific Web pages and actions, SMTP-specific header fields and more.
Security Checking for ID and Password
Survey owners are checked into the administrative portion of the system using their ID and password. This is the only way to access the data collected for the individual survey. UserName and password check is a standard access protocol in the industry.
Access Control for Surveys
Access of potential respondents to the survey can be controlled by password protection. In this way, only a certain group of individuals (that you, as an administrator give access to), are able to take the survey.
This feature is available with the following licenses :

